ETSI has deployed a number of on-line PKI related services in its portal supporting remote plugtest events for checking interoperability on XAdES/CAdES tools. This page provides details of these services and how to use them.
The on-line PKI-related services deployed are listed below:
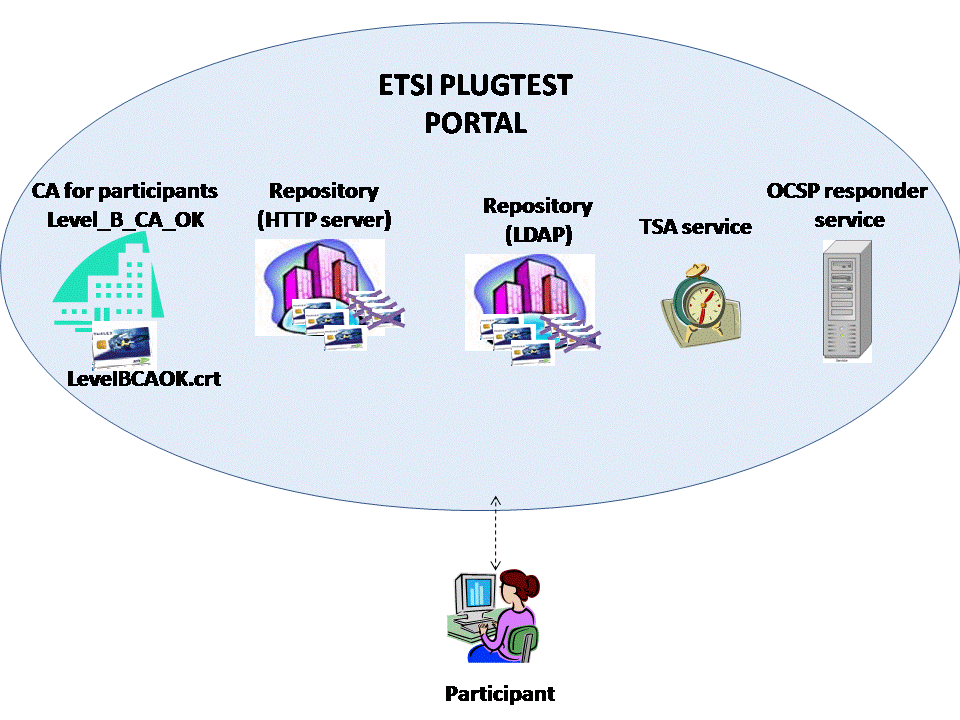
The picture below shows thes on-line services accesible to the users.

Sections below provide details on the aforementioned services, including their location and usage.
The portal incorporates are two different mechanisms for allowing software applications to access the on-line services:
Users should use this service for getting X.509 certificates to be used as signing certificates during the plugtest.
Participants should request certificates and optionally generation of key pairs fulfiling this form.
Alternatively, participants may also request certificates submitting a PKCS#10 file locally generated fulfilling this form.
Participants in XAdES interoperability tests must use two Time-stamp Authority servers for getting RFC-3161 time-stamps.
Details required for accessing the service (host name, port and protocol) required for XAdESv1.3.2 are provided in this page. Link "Online TSP Services access" in left frame of this page points to that page.
For participating in new interoperability tests specific to XAdESv1.4.1, participants must access the service (host name, port and protocol) as detailed in this page. Link "Online TSP Services access for XAdES 141" in left frame of this page points to that page.
The portal deploys a "Direct Trust Model" where each CA acts also as an OCSP server for the certificates that it has issued.
Participants must, in consequence, address the OCSP Request to the issuing CA of the certificate when requesting and OCSP Response with details on its status.
Below follow the addresses where the different CAs may be accessed for requesting OCSP responses:
Address for accessing RootCAOK CA: http://xades-portal.etsi.org/protected/capso/OCSP?ca=RootCAOK.
This CA will generate OCSP responses on the status of LevelACAOK CA and the TSA certificates.
Address for accessing LevelACAOK CA: http://xades-portal.etsi.org/protected/capso/OCSP?ca=LevelACAOK.
This CA will generate OCSP responses on the status of LevelBCAOK CA certificate.
Address for accessing LevelBCAOK CA: http://xades-portal.etsi.org/protected/capso/OCSP?ca=LevelBCAOK.
This CA will generate OCSP responses on the status of participants' certificates and on the certificatse used by ETSI for generating the signatures corresponding to the only-verification test cases.
Address for accessing RootCA2OK CA: http://xades-portal.etsi.org/protected/capso/OCSP?ca=RootCA2OK.
This CA will generate OCSP responses on the status of the TSA2 certificates.
The list of addresses to the different CAs may be found in this page of the portal.
Users may use this service for getting access to CA and TSA certificates, and CRLs during the plugtest.
Below follows the URL where this service is accessible:
ldap://xades-portal.etsi.org:389
The directory may be browsed using any LDAP client. e.g. Apache Directory Studio.
Users may also use this service for getting access to CA and TSA certificates, and CRLs during the plugtest.
CA and TSA certificates may be accessed at this URL.
CRLs may be accessed at this URL.